Teknik Routing Internet
Onno W. Purbo
Konsep IP address, network address, subnet mask, broadcast address merupakan dasar
dari teknik routing di Internet. Untuk memahami ini semua kemampuan matematika
khususnya matematika boolean, atau matematika binary akan sangat membantu
memahami konsep routing Internet. Contoh pertanyaan yang sering dilontarkan,
· Mengapa kita memilih IP address 192.168.1.5?
· Mengapa subnet mask yang digunakan 255.255.255.224? mengapa bukan angka
lain?
· Mengapa network address 167.205.10.0?
· Mengapa broadcast address-nya 202.159.32.15?
· Dll.
Bagaimana menentukan semua alamat-alamat tersebut? Hal tersebut yang akan dicoba
dijelaskan secara sederhana dalam tulisan ini.
Kalkulator - Alat bantu yang dibutuhkan
Untuk memudahkan kehidupan anda, ada
baiknya menggunakan fasilitas kalkulator yang
ada di Windows. Di Windows 98 dapat di
akses melalui Start Programs
Accessories Calculator.
Calculator
yang standar
memang
sulit
digunakan
untuk
membantu
kalkulasi
biner, oleh
karena itu
pilih View
Scientific
untuk
memperoleh
tampilan
kalkulator
scientifik
yang dapat
digunakan untuk perhitungan biner.
Dengan cara
memindah
mode
operasi ke
bin, maka
nilai yang
ada akan
berubah
menjadi
binary. Pada
gambar
contoh
diperlihatka
n nilai awal
15 desimal,
di pindahkan
menjadi
1111 binary.
Sedikit Aljabar Boolean
Aljabar boolean adalah teknik menghitung dalam bilangan binary 101010111 dsb. Proses
konversi dari desimal ke binary sudah tidak perlu kita pikirkan lagi karena sudah dibantu
menggunakan kalkulator yang ada di Windows 98.
Dari sekian banyak fungsi yang ada di aljabar boolean, seperti and, or, xor, not dll., untuk
keperluan teknik routing di Internet, kita hanya memerlukan fungsi “dan” atau “and”.
Contoh,
1 and 1 = 1
1 and 0 = 0
0 and 1 = 0
0 and 0 = 0
atau yang lebih kompleks
11001010.10011111.00010111.00101101
di AND dengan
11111111.11111111.11111111.00000000
menjadi
11001010.10011111.00010111.00000000
Tidak percaya? Coba saja masukan angka-angka di atas ke kalkulator Windows, anda
akan memperoleh hasil persis seperti tertera di atas. Pusing? Mari kita konversikan
bilangan binary di atas menjadi bilangan desimal supaya anda tidak terlalu pusing melihat
angka 10101 dsb. Dalam notasi desimal, kalimat di atas menjadi,
202.159.23.45
di AND dengan
255.255.255.0
menjadi
202.159.23.0
Cukup familiar? Coba perhatikan nilai-nilai alamat IP yang biasa kita masukan di Start
Settings Control Panel Network TCP/IP Properties.
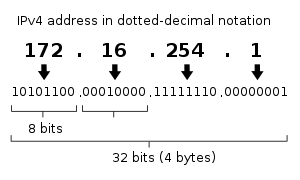
Kalau kita perhatikan baik-baik maka panjang sebuah alamat IP adalah 32 bit, yang
dibagi dalam empat (4) segmen yang di beri tanda titik “.” antar segmen-nya. Artinya
setiap segmen terdapat delapan (8) bit.
Alokasi jumlah alamat IP di Jaringan
Teknik subnet merupakan cara yang biasa digunakan untuk mengalokasikan sejumlah
alamat IP di sebuah jaringan (LAN atau WAN). Teknik subnet menjadi penting bila kita
mempunyai alokasi IP yang terbatas misalnya hanya ada 200 IP yang akan di
distribusikan ke beberapa LAN.
Untuk memberikan gambaran, misalkan kita mempunyai alokasi alamat IP dari
192.168.1.0 s/d 192.168.1.255 untuk 254 host, maka parameter yang digunakan untuk
alokasi adalah:
192.168.1.255 – broadcast address LAN
255.255.255.0 - subnet mask LAN
192.168.1.0 – netwok address LAN.
192.168.1.25 – contoh IP address salah workstation di LAN.
Perhatikan bahwa,
· Alamat IP yang pertama 192.168.1.0 tidak digunakan untuk workstation, tapi
untuk menginformasikan bahwa LAN tersebut menggunakan alamat 192.168.1.0.
Istilah keren-nya alamat IP 192.168.1.0 di sebut network address.
· Alamat IP yang terakhir 192.168.1.255 juga tidak digunakan untuk workstation,
tapi digunakan untuk alamat broadcast. Alamat broadcast digunakan untuk
memberikan informasi ke seluruh workstation yang berada di network
192.168.1.0 tersebut. Contoh informasi broadcast adalah informasi routing
menggunakan Routing Information Protocol (RIP).
· Subnet mask LAN 255.255.255.0, dalam bahasa yang sederhana dapat di
terjemahkan bahwa setiap bit “1” menunjukan posisi network address, sedang
setiap bit “0” menunjukan posisi host address.
Konsep network address & host address menjadi penting sekali berkaitan erat dengan
subnet mask. Perhatikan dari contoh di atas maka alamat yang digunakan adalah
192.168.1.0 network address
192.168.1.1 host ke 1
192.168.1.2 host ke 2
192.168.1.3 host ke 3
……
192.168.1.254 host ke 254
192.168.1.255 broacast address
Perhatikan bahwa angka 192.168.1 tidak pernah berubah sama sekali. Hal ini
menyebabkan network address yang digunakan 192.168.1.0. Jika diperhatikan maka
192.168.1 terdiri dari 24 bit yang konstan tidak berubah, hanya delapan (8) bit terakhir
yang berubah memberikan identifikasi mesin yang mana. Tidak heran kalau netmask
yang digunakan adalah
(binary) 11111111.11111111.11111111.00000000
(desimal) 255.255.255.0.
Walaupun alamat IP workstation tetap, tapi netmask yang digunakan di masing-masing
router akan berubah-ubah tergantung posisi router dalam jaringan. Bingung? Mari kita
lihat analogi di jaringan telepon yang biasa kita gunakan sehari-hari, misalnya kita
mempunyai nomor telepon yang dapat di telepon dari luar negeri dengan nomor,
+62 21 420 1234
Lokasi nomor telepon tersebut di Jakarta, dengan sentral sekitar senen & cempaka putih.
Kita perhatikan perilaku sentral telepon di tiga lokasi
1. Sentral di Amerika Serikat
2. Sentral di Indosat Jakarta
3. Sentral telepon di Telkom Jakarta Gatot Subroto
4. Sentral telepon di Senen, Cempaka Putih.
Pada saat kawan kita di amerika serikat akan menghubungi rekannya di Jakarta dengan
nomor +62 21 420 1234.
Pada sentral di Amerika Serikat, hanya memperhatikan dua digit pertama (+62), setelah
membaca angka +62 tanpa memperdulikan angka selanjutnya maka sentral di Amerika
Serikat akan menghubungi gerbang SLI di Indosat Jakarta untuk memperoleh
sambungan. Perhatikan di sini netmask di sentral amerika serikat untuk jaringan di
Indonesia hanya cukup dua digit pertama, selebihnya di anggap host (handset) di jaringan
telepon Indonesia yang tidak perlu di perdulikan oleh sentral di Amerika Serikat.
Pada sentral Indosat Jakarta, berbeda dengan sentral di Amerika Serikat, akan
memperhatikan dua digit selanjutnya (jadi total +62 21). Dari informasi tersebut sentral
indosat mengetahui bahwa trafik tersebut untuk Jakarta dan akan meneruskan trafik ke
sentral Telkom di Jl. Gatot Subroto di Jakarta. Perhatikan sekarang netmask menjadi
empat (4) digit.
Pada sentral Telkom di Gatot Subroto Jakarta akan melihat tiga (3) digit selanjutnya
(+62 21 420). Dari informasi tersebut maka sentral Telkom Gatot Subroto akan
meneruskan trafik ke sentral yang lebih rendah kemungkinan di Gambir atau sekitar
Senen. Perhatikan sekarang netmask menjadi tujuh (7) digit.
Pada sentral terakhir di Gambir atau Senen, akan dilihat pelanggan mana yang di tuju
yang terdapat dalam empat digit terakhir (1234). Maka sampailah trafik ke tujuan. Nomor
pelanggan kira-kira ekuivalen dengan host address di jaringan Internet.
Mudah-mudahan menjadi lebih jelas fungsi netmask. Secara sederhana netmask
digunakan untuk memisahkan antara network address & host address untuk memudahkan
proses routing di jaringan Internet. Dengan adanya netmask kita tidak perlu
memperhatikan seluruh alamat IP yang ada, tapi cukup memperhatikan segelintir network
address saja.
Beberapa contoh network address di Internet di Indonesia, dapat dengan mudah
mengidentifikasi ISP atau pemilik jaringan tersebut, misalnya,
202.134.0.0 telkom.net
202.154.0.0 rad.net.id
202.159.0.0 indo.net.id
202.158.0.0 cbn.net.id
167.205.0.0 itb.ac.id
terlihat jelas bahwa terdapat sebuah struktur penomoran, terlihat sekali bahwa IP address
dengan awalan 202 umumnya ISP dari Indonesia yang di alokasikan oleh penguasa IP di
Internet seperti www.icann.org. Dengan teknik ini sebetulnya dari Internet untuk
mengarah ke Indonesia cukup melakukan masking dengan mask
255.0.0.0
karena delapan (8) bit pertama yang perlu di mask. Biasanya pada router dapat juga di
tulis dengan kalimat
202.159.0.0/8
ada slash /8 di belakang IP address menandakan bahwa cukup delapan (8) bit pertama
yang perlu diperhatikan.
Selanjutnya untuk mengarahkan paket data ke jaringan internal di IndoNet (indo.net.id),
maka masking pada router di IndoNet atau berbagai ISP di Jakarta adalah
255.255.0.0
atau pada router tersebut dapat digunakan routing ke arah
202.159.0.0/16
perhatikan sekarang slash yang digunakan adalah slah 16 (/16), artinya cukup
diperhatikan 16 bit saja dari total 32 bit IP address yang ada.
Selanjutnya mengarahkan paket ke PT. Antah Berantah yang memiliki sambungan leased
line di IndoNet, pada router di IndoNet dapat digunakan masking yang tidak terlalu
normal misalnya
255.255.255.240
atau dapat digunakan pengalamatan
202.159.12.0/24
artinya router harus memperhatikan 24 bit pertama dari IP address.
Sintaks Penambahan Route
Setelah kita mengetahui pola fikir routing pada Internet, maka langkah selanjutnya yang
perlu kita tahu adalah cara menambahkan route pada tabel route di komputer. Hal ini
tidak terlalu sukar, perintah yang dapat digunakan adalah
C:> route (di Windows)
# route (di Linux)
di Windows format penambahan route tersebut sangat sederhana yaitu
C:> route add 202.159.0.0 netmask 255.255.0.0 192.168.0.1 metric 3
Di Linux format-nya dapat menjadi
# route add –net 202.159.0.0/16 gw 192.168.0.1 metric 3
Dimana 202.159.0.0 adalah network address (dapat juga kalau dibutuhkan kita
memberikan routing ke sebuah host); 255.255.0.0 atau /16 adalah netmask yang
digunakan; 192.168.0.1 adalah gateway yang digunakan; metric 3 menandakan prioritas
routing, yang dapat dikosongkan saja.
Untuk melihat tabel routing di komputer kita dapat dilakukan dengan perintah
C:> netstat –nr (di Windows)
C:> route print (di Windows)
# netstat –nr (di Linux)
# route (di Linux)
Tentunya akan pusing kepala jika kita beroperasi pada jaringan yang kompleks.
Sebaiknya kita menggunakan teknik routing yang automatis. Hal ini dapat dilakukan
dengan mudah di Linux dengan menjalankan software seperti
# routed
atau
# gated
software routing seperti ini mungkin ada di Windows NT atau Windows 2000, tapi tidak
pada Windows 98.